When you implement StoreFront and NetScaler Gateway with Citrix new Federate Authentication Service (FAS) for SAML authentication you almost inevitable will face the “You cannot login using smart card. Please close your browser to protect your account” error after you logout from StoreFront.
Update: Native Solution
In the meantime Citrix implemented their own solution for this – which is of course the preferred solution compared to my rewrites below!
On StoreFront just:
- Edit “C:\inetpub\wwwroot\Citrix\<StoreName>Web\custom\script.js”
- Insert “CTXS.allowReloginWithoutBrowserClose = true”
Source: https://support.citrix.com/article/CTX227673
Background
This message typically pops up after you logout. You’ll first receive the following message asking you to close your browser.
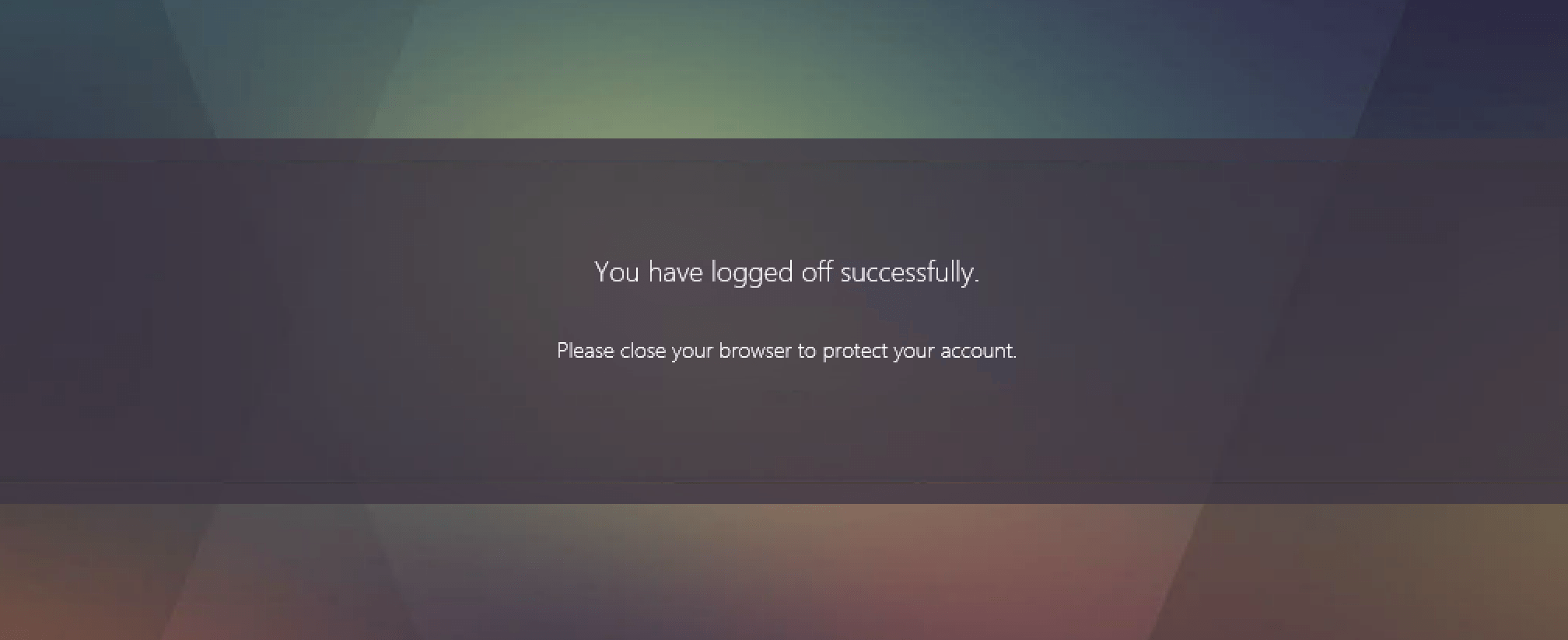
Once you then refresh the page or browse to the StoreFront again without closing your browser you’ll receive the message “You cannot login using smart card”.
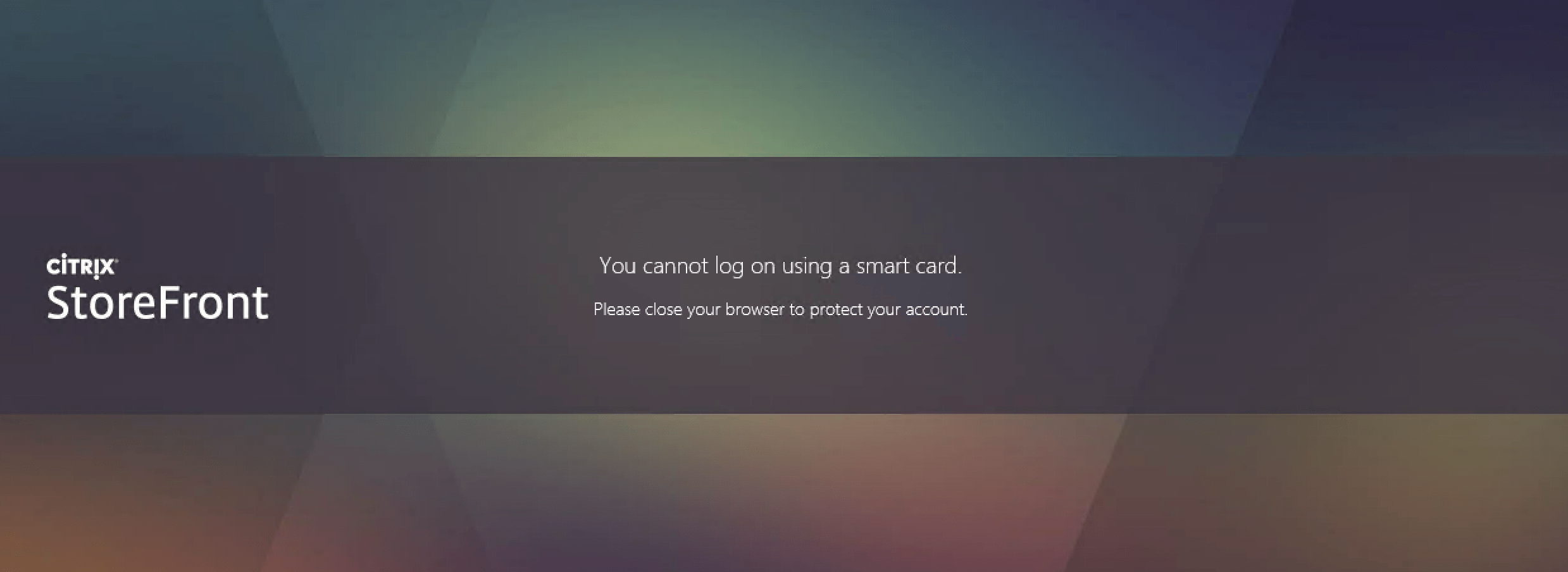
While this is an intended protection mechanism the wording is just confusing for users. The basic intention is to make the user close the browser for security purposes. However, the user doesn’t know about the SmartCard tricks FAS is performing internally.
Solution
StoreFront is handling this protection by setting and checking some cookies. And there are actually two cookies, one that’s asking the user to close the browser and one that’s causing the smart card error.
Now if we delete the cookie responsible for the smart card message the user will get the message just telling him to close the browser instead of a misleading “You cannot login using smart card”.

We can achieve this on NetScaler using the following simple rewrite on the logout page that’ll invalidate the corresponding cookie:
You’ll need to edit the /Citrix/StoreWeb paths accordingly
add rewrite action rw.act.expire-smartcard-cookie insert_http_header "Set-Cookie" ""CtxsSmartcardAuthenticated=xyz;Path=/Citrix/<strong>StoreWeb</strong>/;expires=Wednesday, 09-Nov-1999 23:12:40 GMT; Secure""
add rewrite policy rw.pol.expire-smartcard-cookie.logout "HTTP.REQ.URL.PATH.SET_TEXT_MODE(IGNORECASE).EQ("/Citrix/<strong>StoreWeb</strong>/logout.aspx")" rw.act.expire-smartcard-cookie
bind vpn vserver ngw.vs.citrix.nerdscaler.lab.ssl.443 -policy rw.pol.expire-smartcard-cookie.logout -priority 100 -gotoPriorityExpression NEXT -type RESPONSE
I’ve noticed that this change doesn’t seem to work with the latest Internet Explorer. This seems to be due to the fact that the logout.aspx is called from within a JavaScript and the browser itself never navigates to that site. IE receives the Cookie expiration but doesn’t seem to react to it within JavaScript.
Optional
If you want to get rid of the browser close message as well you can also remove the cookie causing this. You can do this using the following rewrite.
add rewrite action rw.act.expire-browserclose-cookie insert_http_header "Set-Cookie" ""CtxsBrowserCloseToEndSession=xyz;Path=/Citrix/<strong>StoreWeb</strong>;expires=Wednesday, 09-Nov-1999 23:12:40 GMT; Secure""
add rewrite policy rw.pol.expire-browserclose-cookie.logout "HTTP.REQ.URL.PATH.SET_TEXT_MODE(IGNORECASE).EQ("/Citrix/<strong>StoreWeb</strong>/logout.aspx")" rw.act.expire-browserclose-cookie
bind vpn vserver ngw.vs.citrix.nerdscaler.lab.ssl.443 -policy rw.pol.expire-browserclose-cookie.logout -priority 110 -gotoPriorityExpression NEXT -type RESPONSE
Warning: StoreFront forces the user to close the session for a reason. The browser closure prevents situations where you logout from StoreFront but not from the IDP.
Let’s say you’re using a shared computer. You log off your StoreFront and you don’t close the browser. Chances are you’re still logged into your IDP at this stage. Now if the next user browses to StoreFront he’ll get logged into your account straight away as you’re still authenticated with the IDP.
Hi,
This solution does only work with Chrome at the moment. Both IE and Firefox does not delete the CtxsSmartcardAuthenticated cookie. Is there any other way to force removal of this cookie? For example a redirect to anoter web-page that invalidates the cookie?
Regards
Alexander
LikeLike
Yes, I’ve noticed that as well.
I’ve tried redirects but one problem with them is that the whole StoreFront website is only AJAX calls. Including the logoff. So the logoff is just client-side JS calling one website. And if you give JS a redirect it won’t happen.
One other option I thought about is actually re-writing StoreFronts JS logic and hook into the functions behind the logout process and delete the cookies from there. But that’s a lot of reverse-engineering and I haven’t had the patience and time for that yet.
Manuel
LikeLike
It should be: “CtxsSmartcardAuthenticated=xyz;Path=/Citrix/StoreWeb/;
If you use the “/” at the end because the CtxsSmartcardAuthenticated cookie created by StoreFront will be bind to the /Citrix/StoreWeb/ path instead of without the slash. It works for IE,Edge, Chrome & FireFox
LikeLike
Thanks Rick, much appreciated and corrected!
Worked for me in the past without the slash as well though – can’t recall which browsers I’ve tested.
LikeLike
I coudn’t get it running with the setting in script.js on storefront.
But it turns out, you can add the entry(CTXS.allowReloginWithoutBrowserClose = true) to script.js on /var/netscaler/logon/LogonPoint/custom. This works for all browser.
LikeLike
Marco, I tested this on Storefront version 3.13.0.16017 successfully and it worked for Chrome, IE, Microsoft Edge and Microsoft Edge Chromium.
What version of storefront did you test on?
LikeLike
https://support.citrix.com/article/CTX227673, states this behavior is by design. Should we be changing this as on shared computers there maybe a security risk?
LikeLike
Hi Rashannw, absolutely agreed! This option should be treated with care as stated in my “Warning” section at the bottom of the article.
LikeLike
Not sure if this threat is still active, will give it a try
First https://support.citrix.com/article/CTX227673 does not work for me. I addedd to both Storefront and ADC – the same message
I tried rewrite policy – ig et the following error:
> add rewrite action rw.act.expire-smartcard-cookie insert_http_header “Set-Cookie” “”CtxsSmartcardAuthenticated=xyz;Path=/Citrix/CAGsamltestWeb/;expires=Wednesday, 09-Nov-1999 23:12:40 GMT; Secure””
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
ERROR: No such argument [CtxsSmartcardAuthenticated=xyz]
What I am doing wrong?
Thank you
LikeLike